Default Constraints allow admins to conveniently apply policies to all OPA enabled clusters This would allow admins an easier way to make sure all user clusters are following some policies (for example security), instead of the current way in which Constraints need to be created for each cluster separately. Kubermatic operator/admin creates a Constraint in the admin panel, it gets propagated to seed clusters and user clusters with OPA-integration
Create Default Constraint
In the Admin view navigate to the OPA menu and then to Default Constraints.
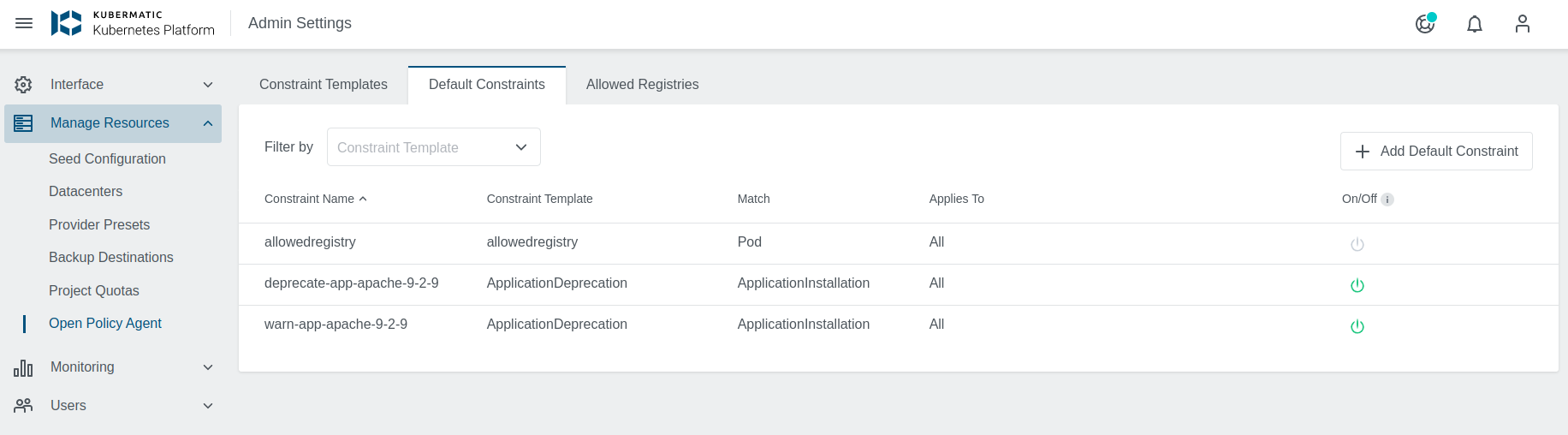 To add a new default constraint click on the
To add a new default constraint click on the +Add Default Constraint icon on the right. A new dialog will appear, where you can specify the name, the constraint template and the spec:
constraintType: K8sPSPAllowPrivilegeEscalationContainer
match:
kinds:
- kinds:
- Pod
apiGroups:
- ''
labelSelector: {}
namespaceSelector: {}
selector:
labelSelector: {}
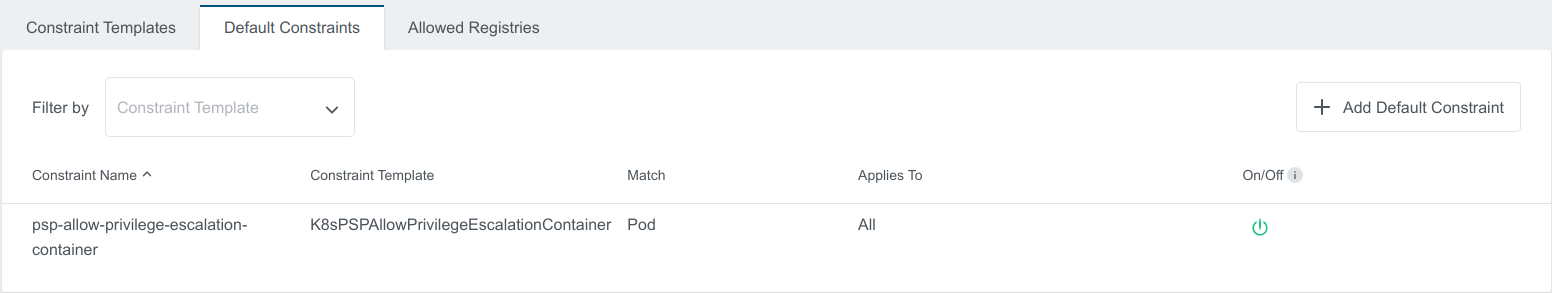
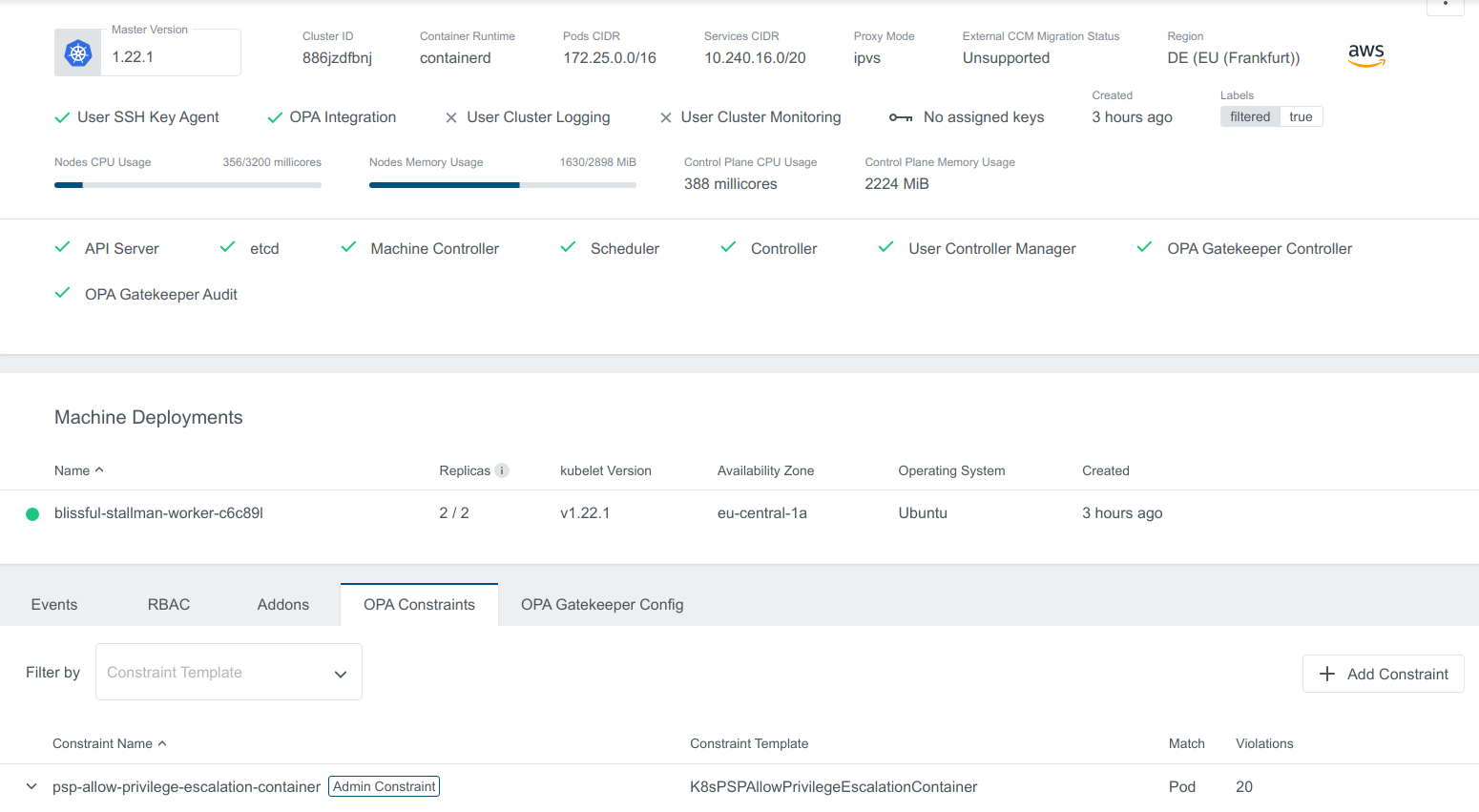
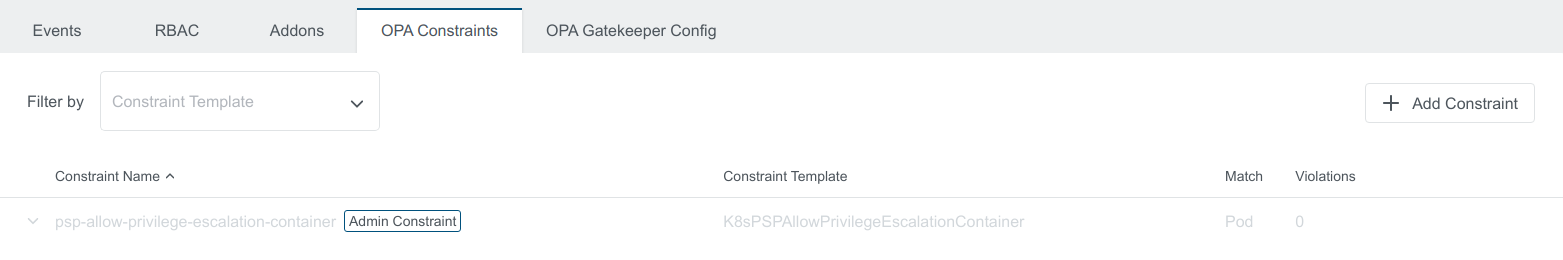
The Default Constraint created will also show up in the applied cluster view with Admin Constraint label
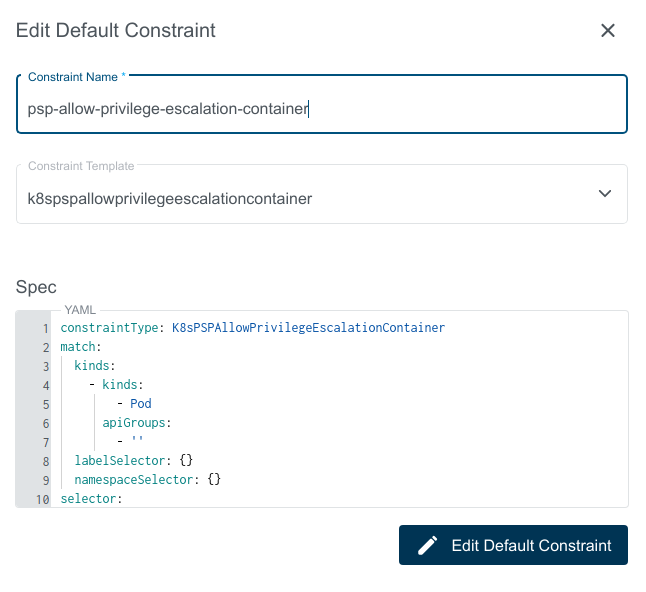
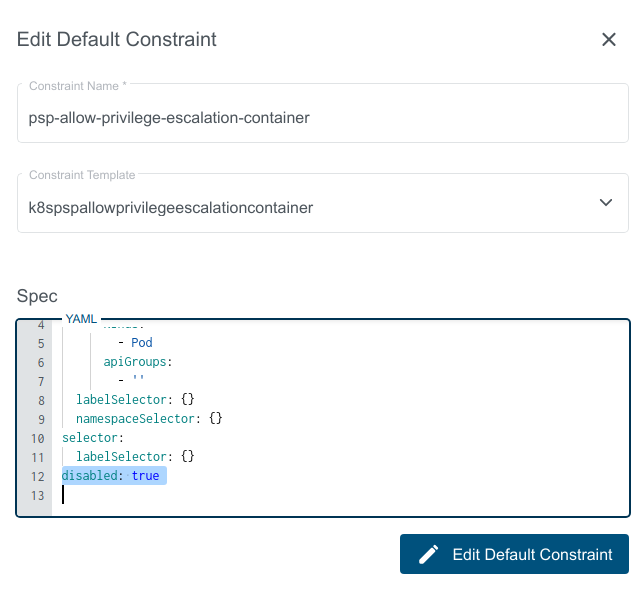
Edit Default Constraint
Editing Default Constraint will sync the changes to all the respective constraints on the user clusters.
To edit the constraint click on edit button on the right that appears when hovering over one of the rows.
In the appearing dialog you can now edit the Default Constraint.
Filtering Clusters on Default Constraints
This is an EE feature.
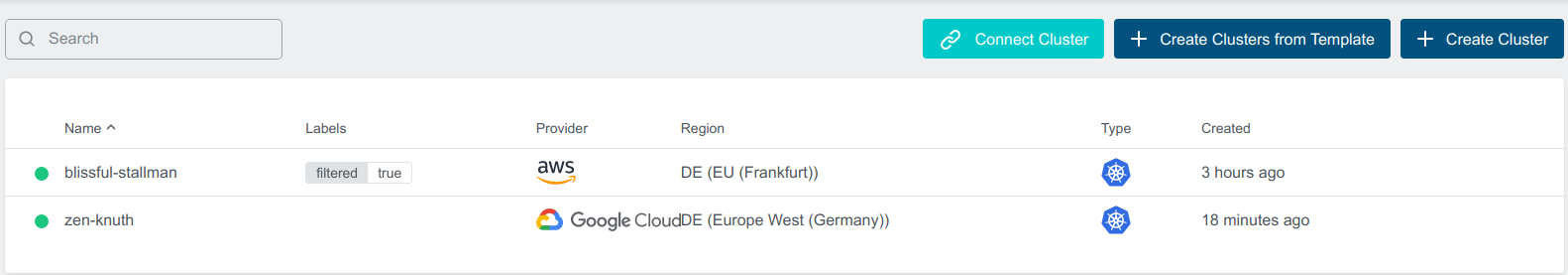
Filter Clusters feature enables Admin to filter User Clusters where Default Constraint is applied using with Cloud Provider and Label Selector filters.
In case of no filtering applied Default Constraints are synced to all User Clusters which can be verified by the Applies To field as shown here:

for example, Admin wants to apply a policy only on clusters with the provider as aws and label selector as filtered:true
To enable this add the following selectors in the constraint spec for the above use case.
selector:
providers:
- aws
labelSelector:
matchLabels:
filtered: 'true'

Constraints then can only be seen in the clusters which satisfy the filters.
for example, for the above use case Default Constraints will be applied to Cluster blissful-stallman with Provider aws and filter filtered: 'true' and not on the Cluster zen-knuth with Provider gcp
Disable Default Constraints
In Admin View to disable Default Constraints, click on the green button under On/Off
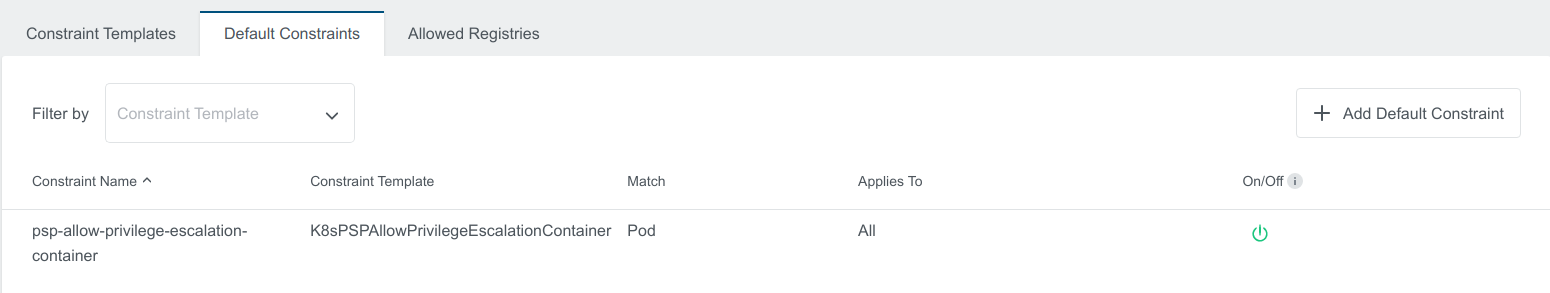
Kubermatic adds a label disabled: true to the Disabled Constraint
Disabled Constraint in the Applied cluster View
disabled-default-constraint-cluster-view.png
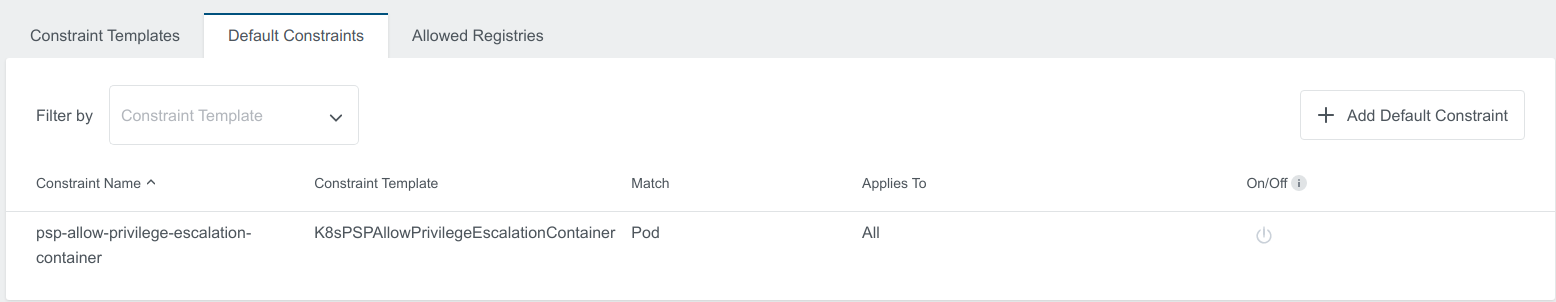
Enable the constraint by clicking the same button
Delete Default Constraint
Deleting Default Constraint causes all related Constraints on the user clusters to be deleted as well.
To delete the constraint click on delete button on the right that appears when hovering over one of the rows.
